Edward G., Cybersecurity and Publisher at Atlas VPN
If you have been following the cybercrime landscape for the past year or so, you must have read about the Conti ransomware group – one of the largest organized crime groups operating at this time.
They have made a name for themselves by extorting large sums of money from over 700 enterprises since 2020. However, things have been going downhill for Conti after they recently got the taste of their own medicine.
On February 25, 2022, the group made a public statement in which they announced that they stand in full support of Russia in light of current events.
The stance ruffled some feathers, and just a few days later, on February 27, a new Twitter account called “ContiLeaks” popped up and began sharing sensitive information about Conti.
ContiLeaks, a rumored Ukrainian security researcher, released a massive record including hundreds of thousands of messages between members of the group.
The Check Point Research team and Brian Krebs took it upon themselves to scan the enormous volume of messages to get insights into the group’s operational activities.
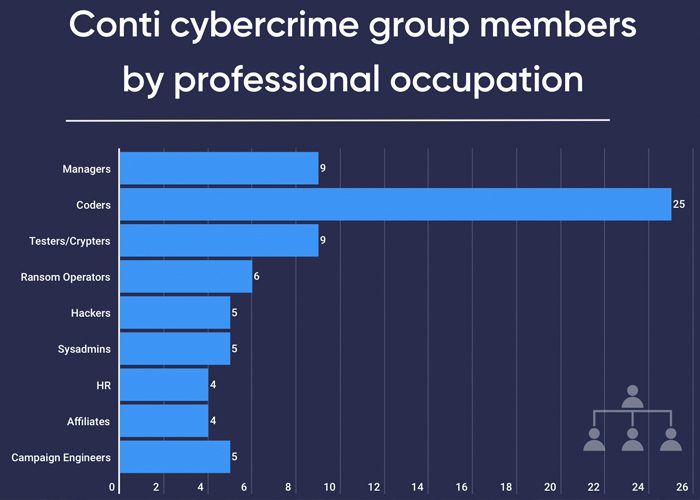
Here, Atlas VPN will distill the data even further to clearly show what the “office” of one of the largest, if not the largest, cybercrime groups looks like. Naturally, a significant portion of senders’ professional occupations remained unidentified, but the picture is rather clear nonetheless.

As per the chart above, coders compose the backbone of Conti. Coders are in charge of the nuts and bolts of the actual malware code, which is central to their whole ransomware operation.
Conti also has at least 9 testers and crypters, without whom it would be nearly impossible to deliver the malware. They work hand-in-hand to create solutions to allow the virus to pass through the latest security measures.
Testers run the malware through various security solutions they expect to encounter when attacking their target company. On the other hand, crypters are responsible for the obfuscation, which will allow the virus to slip through those solutions.
Crypters obfuscate the virus by making syntactic changes to payloads, binaries, and scripts to make them more difficult to detect and analyze.
You can also find at least 6 ransomware operators inside Conti. Operators are the landline between the victim and the group. They speak directly with the victim representatives to negotiate the ransom and the process of payment.
Operators also gather information about the company’s health which allows them to set the perfect ransom amount. If the company states that they don’t have sufficient funds to cover the ransom, then operators can pull out this card.
Like any other “tech” company, Conti has human resource staff, sysadmins, and affiliates.
Salaries at Conti
Some members, such as ransomware operators, are compensated through commissions, computed as a percentage of the paid ransom amount and range between 0.5% and 1%. Managers and programmers tend to get regular salaries. Payments are made once or twice a month in Bitcoin.
Like most other businesses, Conti offers bonuses for its top employees. What is outside of the norm is salary cuts due to underperformance. This would be against the law for companies that operate legally.
Also, logs from leaked messages reveal that even before getting hacked, the Conti group was dealing with internal issues and was struggling to pay their employees. One of their bosses went missing, supposedly due to increased public attention.
In short, it appears that it will be a while until Conti recovers and it is unlikely that we will see any major activity in the next couple of months.